
Resolving a Remote Code Execution Exploit
Table of Contents
Overview
We recently identified potential exploits that:
- Enable an attacker to execute arbitrary code on your Magento server.
- Create files with a .csv extension, create writable directories, and change the permission of existing files to world-writable (777).
Creating files with a .csv extension can lead to executing files like php.csv (only under circumstances discussed in this article). The ability to run code with a .csv extension is dangerous itself and could be combined with other attacks; for example, targeting other software installed on the server.
You can resolve this issue by changing your server's configuration as discussed in Resolving the File System Vulnerability.
Although Magento code is protected by a hash value, the possibility of a successful exploit cannot be eliminated because of the low entropy of the hash secret value.
We strongly recommend you to take precautions discussed in this article and apply a patch for your version of Magento Enterprise Edition or Community Edition.
Versions Affected
Magento software versions affected: The issue affects all shipping versions of Magento Community Edition (CE) and Enterprise Edition (EE).
Operating system versions affected:
- CentOS 5.x and 6.x
- RedHat Enterprise Linux 5.x and 6.x
Getting the Patch
The following table shows the patch you should get for your version of CE or EE.
| Version | Patch |
|---|---|
| EE 1.13 and 1.14, CE 1.8 and 1.9 | SUPEE-1533_EE_1.13.x_v1.patch |
| EE 1.12, CE 1.7 | SUPEE-1533_EE_1.12.x_v1.patch |
| EE 1.11, CE 1.6 | SUPEE-1533_EE_1.11.x_v1.patch |
| EE 1.10.1, CE 1.5.1 | SUPEE-1533_EE_1.10.1.x_v1.patch |
| EE 1.10.0.1, CE 1.5.0.1 | SUPEE-1533_EE_1.10.0.x_v1.patch |
| EE 1.9 | SUPEE-1533_EE_1.9.x_v1.patch |
To get and apply your patch, see How to Apply and Revert Magento Patches.
Determining Your Vulnerability to the File System Attack
To determine if you're vulnerable to execution of PHP code with a non-PHP extension, search your web server configuration file for the following string:
AddHandler application/x-httpd-php .php
The Apache configuration file is typically /etc/httpd/conf/httpd.conf
To confirm you're vulnerable:
- Create a file named test.php.csv anywhere in your web server's doocroot with the following
contents:
<?php phpinfo()
- In a web browser, display that page. (For example, http://www.example.com/path/test.php.csv
- If your browser saves the file or prompts you to save the file instead of displaying it, your server is not vulnerable. You can ignore the rest of this article.
- If a page similar to the following displays, your server is vulnerable. Continue with the next
section.
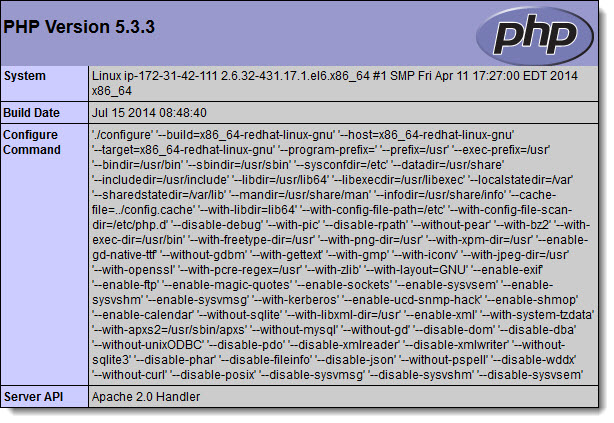
Resolving the File System Vulnerability
To resolve this vulnerability, you must log in to the Magento server as a user with root privileges or as a user with permissions to change the web server configuration.
To resolve the vulnerability:
- Comment out the directive in httpd.conf by preceding it with a pound sign (#) as follows:
# AddHandler application/x-httpd-php .php
- Add a block similar to the following:
<FilesMatch \.php$> SetHandler application/x-httpd-php </FilesMatch>
Some operating systems, like Red Hat Enterprise, might require different syntax such as:<FilesMatch \.php$> SetHandler php5-script </FilesMatch>The regular expression in this setting matches .php only to the final extension in the file name, applying the handler only to PHP files and preventing PHP from executing.